The SS7 protocol was completely closed and protected from external attacks at the development stage. As the technology has become more advanced, the vulnerability of this signaling system has increased. Nowadays, anyone with powerful computer technology and highly specialized knowledge can connect to it and intercept the personal data of the target subscriber along with the verification code for logging in to FB account.

Hacking Facebook via SS7: Attacking Approach
Positive Technologies specialists were the first to mention the SS7 protocol vulnerability. They have also successfully conducted a series of tests to reveal a subscriber's location and make his device inaccessible to the cellular network as well as intercept the messages, incoming and outgoing calls, forge a USSD request and use it to withdraw funds from the target account.
The research has shown that attackers don't even need sophisticated equipment to successfully intercept targeted information. A desktop or a laptop is enough to control a Unix-like operating system based on the Linux kernel and an installed development kit (SDK) that allows you to generate data packets for SS7 protocols. By the way, all the hacking software is freely available, and can be downloaded in 15-20 minutes.
Subscriber's mobility has become the main prerequisite for the emergence and application of the SS7 vulnerability. To fully benefit from cellular communication, a user needs to exchange the data with the operator's towers in real time via the home network and the networks of roaming partners. In this case, not only the subscriber, but also the attacker can be anywhere in the world and at the same time connect to the same nodes of the telephone network. Subscriber will receive his data while the attacker will intercept them.
Intercepting a Facebook Verification Code: The Stages of Attack
You can hack a Facebook account exploiting the SS7 vulnerability to intercept the message with the verification code and, using the password copied from the SMS, gain access to the landing page on the social network. To do this, you should follow the following steps:
1. Connect to the network and get a real MSC/VLR billing address to find out the current location of the target subscriber.
2. Get the subscriber's IMSI (international SIM card identifier).
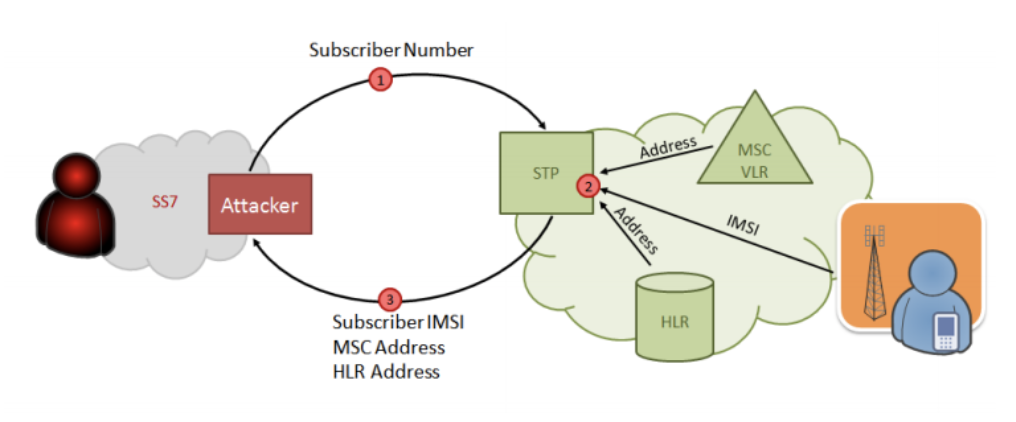
3. Create a fake MSC/VLR billing address and re-register the subscriber in his coverage area.
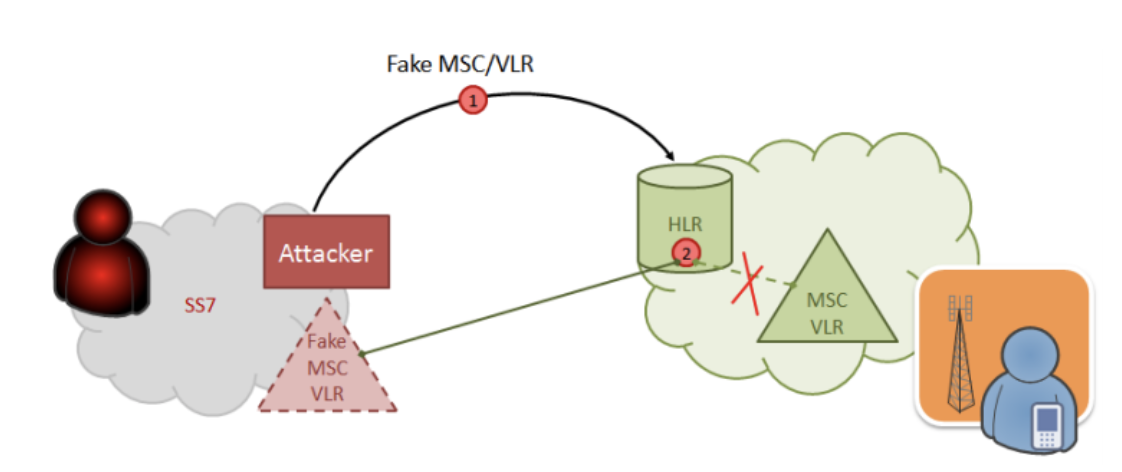
4. After registering the subscriber in the created network, a user will get access to all the incoming and outgoing information and intercept the Facebook verification code.
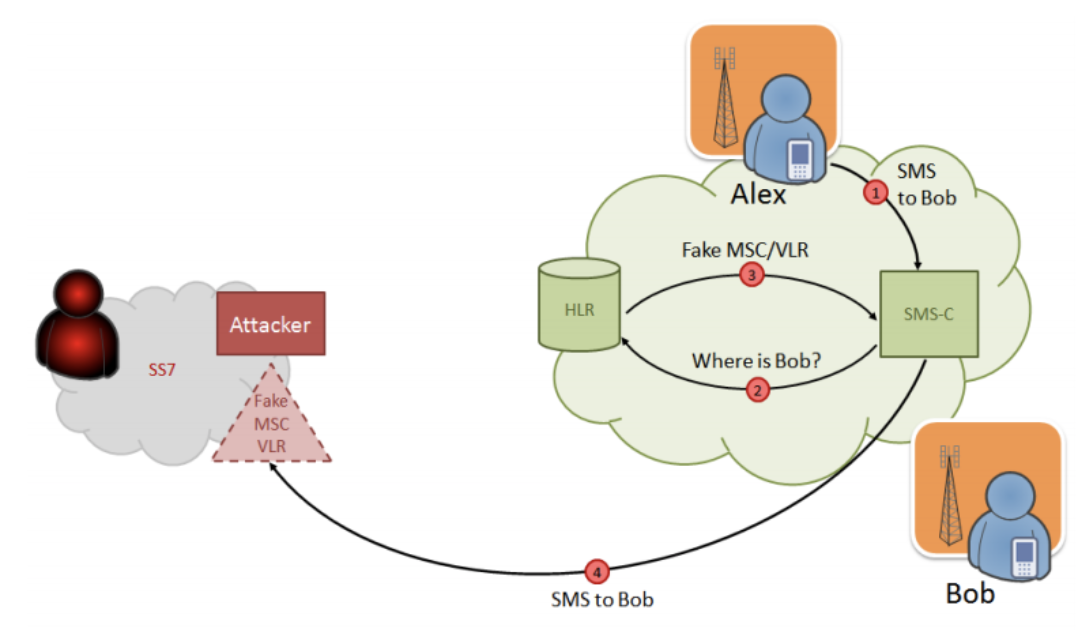
The presented approach makes it possible to intercept incoming and outgoing SMS and change their content as well as send the reports on the receipt and reading of messages, and confirm successful SMS delivery.
The Complexities of a Real Way of Hacking a Facebook account through the SS7 Protocol Vulnerability
Before conducting an attack, you should get access to the signaling system №7. Only officially registered operators can do this. However, today anyone can register as an official provider of mobile services in almost any third world country.
Therefore, if you have a lot of free time and extensive knowledge in the field of information technology, and also want to independently learn how to hack Facebook , please feel free to use the provided attacking approaches.
Therefore, if you have a lot of free time and extensive knowledge in the field of information technology, and also want to independently learn how to hack Facebook, please feel free to use the provided attacking approaches. FB-Tracker app. It operates automatically and does not involve the user in the hacking process. Hence, a user won't need to look for the necessary software, install and configure it, register as a mobile operator, find the target subscriber's mobile device, collect data from it, create a fake billing address, register the mobile device of interest, and then also monitor the entire incoming information.
FB-Tracker works automatically on a remote server and collects all the necessary information from any Facebook account in about 10 to 15 minutes, providing the users with the readily archived data package. To hack a Facebook account exploiting the SS7 protocol vulnerability, simply enter the landing page URL in the app and click the Launch button. Once the application has successfully gained access to the target account and collected the required data, you will be able to download the generated archive and unpack it on your computer or smartphone.
It is important to remember that using SMS as a part of two-factor authentication has long been recognized as the least secure solution. Fortunately, in some cases, you can opt out of using the text messages. Many applications, instant messengers, social networks and banking institutions offer sending verification codes by mail or in the format of a voice call. Therefore, we recommend using such options, if possible.